Case Summary
Antigen Security was engaged by the victim client to investigate a possible Business Email Compromise. Business Email Compromise (BEC) is a cyberattack involving the hacking or spoofing of a business email address. The victim of a BEC attack typically receives an email that appears to come from a trusted business that looks and feels genuine. But frequently it contains a phishing link, a malicious attachment, or a request to transfer money to the attacker. The client reported receiving multiple such phishing emails including ones with malicious Excel Spreadsheets attached. Following payload execution, “invoice.xls” three dropped files: yhjlswle.vbs, dkwtoaqzbs.hfb, and ughldskbhn.bat on the host, all of whom were quarantined by the endpoint detection and response tool.
During the investigation, Antigen Security assessed with confidence that this was a targeted Emotet malware campaign in which approximately 135 malicious emails were sent to the client’s employees between February 7, 2022 and February 8, 2022. Emails sent by the threat actor were tailored to lure users with factual company details such as specific employee names and facility conference rooms.
The threat actor staged 7 waves of phishing between February 7, 2022 and February 8, 2022. During the first phishing wave, the threat actor successfully lured one employee into opening a suggestively named Excel file embedded with a malicious payload. Many of the later phishing emails contained details that suggested the initial victim user’s email was exfiltrated and incorporated into the subsequent phishing waves based on suggestive email subject lines. The next 6 phishing waves were seen to be unsuccessful. In total, the phishing emails received by the client contained a total of 28 unique phishing malware payloads, 3 unique code blocks, and 43 unique domains used as threat actor infrastructure.
Antigen Security collected triage-level data from the single infected host machine and conducted extensive forensic analysis of the device. Through analysis Antigen Security was unable to identify any evidence of successful lateral movement or signs of persistence. However, upon further review of the different malware targeting the client it was clear to Antigen Security that lateral movement was the threat actor’s intent. Antigen Security confirmed that the EDR tool quarantined the malware before any attempt was successful.
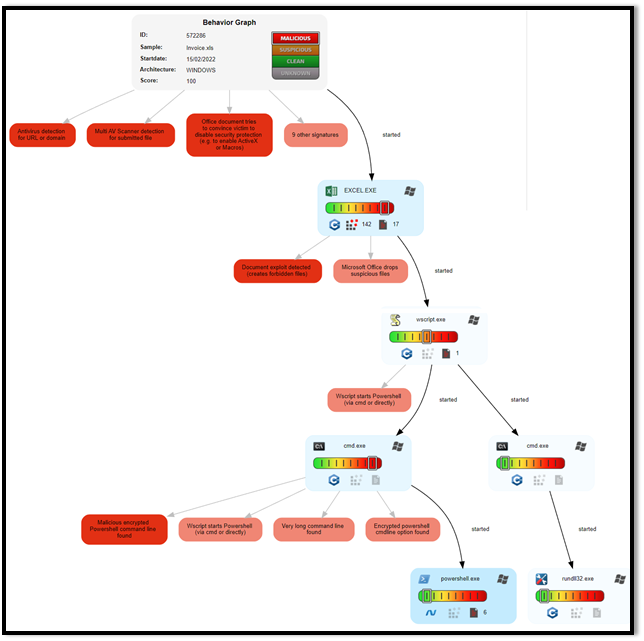
Figure 1: Analysis of Malicious Executable Sent to Client
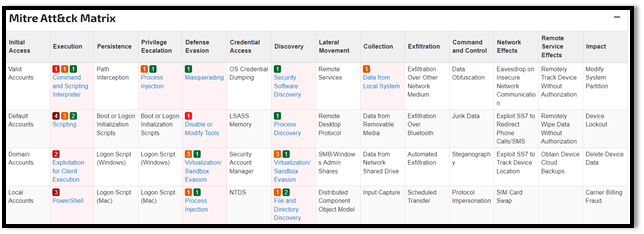
Figure 2: Invoice.xls ATT&CK Matrix
Analyst Comments
The client’s EDR solution played a crucial role in stopping the spread of the Emotet malware. When the malicious executable was opened from the first phishing email, the client’s EDR solution was able to successfully quarantine the malware before it was ever able to run. Had this payload been properly executed, the threat actor would have been able to secure a foothold and laterally move throughout the network. EDR solutions are a great defense against cyber-attacks, particularly when used in tandem with cybersecurity best practices.
- Office365 best practices are the most effective way to avoid a business email compromise.
- Ensure that your users are trained to recognize and easily report phishing attacks and employ strong passwords.
- Enable MFA so that users will have to utilize a 2-step verification at logon.
- Block corporate password reuse to better enable strong passwords and limit the attempts at password guessing from threat actors.
- Deploy an anti-malware solution and deploy anti-phishing defenses.
- Disable basic authentication in order to stop proxy authentication an attacker could leverage. Furthermore, you also want to identify which conditional access policies make sense for your client/company.
- Lastly, ensure that audit logging is turned on to ensure logs are available to review in the event of an incident or for self-auditing.
During the investigation, Antigen identified phishing emails that suggested the initial victim user’s inbox was compromised. However, the second through seventh wave of phish appeared to have email content from the known compromised user’s account seeded in the subject lines, according to the IT staff. If true, it means the threat group ingested the compromised user’s email, parsed the email chains for details, and composed the next wave of tailored emails together with those parsed details in approximately 1 hour based on the observed timeline of events. Achieving that in relatively short window of time would most be most practical via polymorphism, a feature later detailed in the The Hacker News. Rapidly changing tactics mid campaign demonstrates sophistication, but to intelligently automate it via polymorphic code it makes it all the more remarkable.
Get Help from Our Experts
As sophisticated attacks such as BECs have become common, it’s important to be prepared with an incident response plan. Antigen Security can help you determine the next steps in the aftermath of an attack. Schedule a meeting with one of our experts to get started.
Suspicious C2 Domains and IPs
| Domain | Location | ISP Provider | IP |
| https://fullness-safety[.]com/-/P6x/ | United States | CYBERCON | 65.175.118.94 |
| https://nabajyotifoundation[.]com/da8uc7jo/4Za/ | Germany | Contabo GmbH | 178.18.255.145 |
| https://dwwmaster[.]com/wp-content/ebHTB4UF2/ | China | Huawei Cloud Service data center | 121.36.207.120 |
| http://formula8020[.]com/css/56Dzi0P/ | United States | 34.98.99.30 | |
| https://calad-formation[.]fr/r3x94z/kgZ9OGCi/ | France | OVH SAS | 54.36.91.62 |
| http://lissbernardin[.]com/hthjb3i/x9KHpCeYrr/ | United States | GO-DADDY-COM-LLC | 132.148.230.59 |
| http://royalsnackmyanmar[.]com/wp-includes/GMtz6DxM/ | Thailand | GMO-Z com NetDesign Holdings Co., Ltd. | 163.44.198.39 |
| http://pristineservices[.]findfacts[.]co[.]in/cgi-bin/BuLyc2HKLHIQVHQLc/ | India | PUBLIC-DOMAIN-REGISTRY | 103.195.184.162 |
| http://speedrankingsystem[.]de/wp-admin/k63ZcimPsE6/ | Germany | Host Europe GmbH | 92.204.37.72 |
| https://tigela[.]org[.]np/wp-content/Irp27O71/ | United States | LIMESTONENETWORKS | 63.143.33.122 |
| https://royaltyrealtynsb[.]com/backup_1/g51THhhLLUqodx6/ | United States | DIGITALOCEAN-ASN | 142.93.205.206 |
| http://bachilleratoporciclos[.]co/wp-content/PvIIx7/ | United States | GO-DADDY-COM-LLC | 72.167.66.37 |
| https://edu-media[.]cn/wp-admin/cKi/ | China | Hangzhou Alibaba Advertising Co., Ltd. | 123.56.83.149 |
| https://rtd[.]b2bpipe[.]cn/wp-content/8ESRhIJAIRh/ | China | Hangzhou Alibaba Advertising Co., Ltd. | 47.95.142.91 |
| https://youlanda[.]org/eln-images/n8DPZISf/ | United States | INFB2-AS | 66.175.58.9 |
| http://rosevideo[.]net/eln-images/EjdCoMlY8Gy/ | United States | INFB2-AS | 66.175.58.9 |
| http://vbaint[.]com/eln-images/H2pPGte8XzENC/ | United States | INFB2-AS | 66.175.58.9 |
| https://framemakers[.]us/eln-images/U5W2IGE9m8i9h9r/ | United States | INFB2-AS | 66.175.58.9 |
| http://niplaw[.]com/asolidfoundation/yCE9/ | United States | INFB2-AS | 66.175.58.9 |
| http://robertmchilespe[.]com/cgi/3f/ | United States | INFB2-AS | 66.175.58.9 |
| http://vocoptions[.]net/cgi/ifM9R5ylbVpM8hfR/ | United States | INFB2-AS | 66.175.58.9 |
| http://missionnyc[.]org/fonts/JO5/ | United States | INFB2-AS | 66.175.58.9 |
| http://robertflood[.]us/eln-images/DGI2YOkSc99XPO/ | United States | INFB2-AS | 66.175.58.9 |
| http://mpmcomputing[.]com/fonts/fJJrjqpIY3Bt3Q/ | United States | INFB2-AS | 66.175.58.9 |
| http://dadsgetinthegame[.]com/eln-images/tAAUG/ | United States | INFB2-AS | 66.175.58.9 |
| http://smbservices[.]net/cgi/JO01ckuwd/ | United States | INFB2-AS | 66.175.58.9 |
| http://stkpointers[.]com/eln-images/D/ | United States | INFB2-AS | 66.175.58.9 |
| http://rosewoodcraft[.]com/Merchant2/5[.]00/PGqX/ | United States | INFB2-AS | 66.175.58.9 |
| http://santafetortilla[.]com/_baks/tUx9/ | United States | INFB2-AS | 66.175.58.9 |
| http://donbaham[.]com/Home_files/YS0PAZPXcYeraes/ | United States | INFB2-AS | 66.175.58.9 |
| http://barnhart-studios[.]com/eln-images/Vghg1n/ | United States | INFB2-AS | 66.175.58.9 |
| http://blute[.]com/3Dtech/jLu8IAnnj3gK9Wc/ | United States | INFB2-AS | 66.175.58.9 |
| http://zenzebra[.]net/plath/9Q0DBlE/ | United States | INFB2-AS | 66.175.58.9 |
| http://rogerschultz[.]com/eln-images/u0vT/ | United States | INFB2-AS | 66.175.58.9 |
| http://realacorp[.]net/PhotoGallery/UwmRHceSGbaCeGF/ | United States | INFB2-AS | 66.175.58.10 |
| http://miniflam[.]com/eln-images/fSwbQjUMAfGxgdw/ | United States | INFB2-AS | 66.175.58.9 |
| http://marezdecor[.]com/MarezGallery/sEQxWTpMJ7A8rAtY0D/ | United States | INFB2-AS | 66.175.58.9 |
| http://hollywoodvisual[.]com/eln-images/HIWl5z/ | United States | INFB2-AS | 66.175.58.9 |
| http://marcowine[.]com/Images/SLlwnvS7Uxnymm/ | United States | INFB2-AS | 66.175.58.9 |
| http://chpopesco[.]com/Gallery/wPY7j2SE5MIv/ | United States | INFB2-AS | 66.175.58.9 |
| http://modsociete[.]com/cgi/qtAP/ | United States | INFB2-AS | 66.175.58.9 |
| http://boamorph[.]com/cgi/hTa5ip96VSdNjX/ | United States | INFB2-AS | 66.175.58.9 |
| http://annefront[.]com/eln-images/gANlH/ | United States | INFB2-AS | 66.175.58.9 |
IOCs
19eff21c6da7f505333f1cfe83cbbbb98f9d999a yhjlswle.vbs
N/A dkwtoaqzbs.hfb
F487A3876DB9CB4332A7CAD95D6795798812CDA0 ughldskbhn.bat
d0e36133984e3b709a001dd144b087699ab219e1 SURI745522740Xinvoice.xls
bd3623061918dcae9ab33bd85c0d9c3161a7985e 2022_02-XBalance.xls
a084feccc72223893a0a90ccc5aba007fe667c5b POX2022-02-07_1909.xls
45743f2c86f06d92ab462525e0d7e74af48e9022 Invoice.xls
0795979af54712ba36b4bbdac48ec92608d22e4c JPKG33964570.xls
899959ffa8e30daade07fe569402d99b5f45e26a 25947431_Dt_02072022.xls
b2cb19c63e5b1deba78a94f0c56f5e461f204ad0 PaymentXstatus.xls
9fa4f580fc7edf7ddb40671034e351c68a370084 InvoiceX2894350973XX51444212.xls
37ea002cf2690c279060c05cd80b9ce0190275e1 form.xls
62cfd18a51c52ffdbd4a8d8795d3b26d989df0a9 InvoiceXforXpayment.xls
7e912cccfb4e8c274a25c835e8a7a46adfe68ad1 Transaction.xls
18fedfcb99f8c42a87ee73104fa11e2aeb8c0bfd BANKXTRANSFERXCOPYXACH.xls
d94c26f5fab3c4fcfb9512127de57920f865ddd2 INVOICEX2022-02-08_1604.xls
fd429bdb7c0fcf8abf9910fd6bd654e070117687 ACHXPaymentXAdvice.xls
40b591272394f3fb5351bd89ebf9f1ba7c7a31d1 JE0856149308.xls
37ea002cf2690c279060c05cd80b9ce0190275e1 2022_02-XReport.xls
6b122a9dae8561df51674aa187e907ab00b77ac4 2022_02-XStatement.xls
50aabeaf06ab6e639856469a58f5c5ddc727b7a7 paymentsX2022-02-07_1547.xls
a30501cb55be3d9b1ab2c1409e1296c34eb88de9 check.xls
392c39f5c13df58aaa2b2b9f5252bbed0ffa81f0 Report.xls
f90ed89aebf00307104edec3083620a4e11c8d17 FW-9262Xreport.xls
9fc0c6329dd43edc4e672481dee69748ea18c5aa 20142232_Dt_02072022.xls
c7c4ef715d70599dc3f8518cb202afb52bb0831e winmail.dat
c6e361acef905dd1c42d4beb467bacd25da73390 19465779_Dt_02072022.xls
d7dc1602d07d58dfea0d32cc48d57e0d3659fcdb ACHXForm.xls
a9073ef3747f3bd42d926c90815c76d65c105877 ElectronicXform.xls
37ea002cf2690c279060c05cd80b9ce0190275e1 2022_02-XBalanceXXXPaymentXReport.xls
95885fb8aeb7e3d4577df44b7d51f2f98a7bd26d payment.xls
c0625676c00831b394f4017e51f50d92363543d5 77299610_Dt_02072022.xls
d1c1a4553882663d6652189208435ce0e96268d3 InvoiceX5XXXXXXXXXXXXE81199781.xls
Resources
- https://threatpost.com/emotet-spreading-malicious-excel-files/178444/
- https://github.com/pr0xylife/Emotet/blob/main/e4_emotet_09.02.2022.txt
- https://blogs.vmware.com/networkvirtualization/2022/02/emotet-is-not-dead-yet-part-2.html/
- https://thehackernews.com/2022/02/reborn-of-emotet-new-features-of-botnet.html
- https://www.checkpoint.com/press/2022/january-2022s-most-wanted-malware-lokibot-returns-to-the-index-and-emotet-regains-top-spot/
- https://docs.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/secure-your-business-data?view=o365-worldwide
