DIY Ransomware with DeepBlueMagic!
Welcome to the second installment of Antigen Security’s Cyber Pathogenesis Series. This report aims to contribute operational details discovered in Antigen’s own DeepBlueMagic ransomware cases that develop into a DeepBlueMgic’s threat actor profile.
Last month, Heimdal Security released what appears to be the first published report on a new ransomware strain known as DeepBlueMagic. The Heimdal report noted the actor’s use of a legitimate third-party disk encryption tool, BestCrypt from Jetico, at the time.
Antigen Security was contracted to perform a compromise assessment with a retail victim who experienced a DeepBlueMagic attack on August, 9 2021. The majority of system disk evidence was lost as a result of the ransomware event. However, evidence was available for three backup disk images of known compromised servers, VPN logs, network intrusion prevention logs, and firewall logs.
Summary of Observed Events:
Antigen has observed that often DeepBlueMagic will initially utilize remote network authentication to the victim’s VPN appliance using guessed or compromised ‘admin’ Active Directory credentials protected only with single factor authentication. DeepBlueMagic obfuscates their true location by using a variety of Tor nodes and VPN sessions, deliberately avoiding the use of remote shells. These connections represent the sole means of command and control observed in use by the threat actor as well.
In one particular instance, within ten minutes of authenticating to the victim network, DeepBlueMagic moved laterally to the victim domain controller using RDP with user-level AD credentials. The threat actor then executed several command line queries discover user, system, domain, and Active Directory objects.
Privilege escalation to Domain Administrator level privileges was achieved by the threat actor within seventeen minutes from initial access event. With Domain Admin privileges in hand and the network sufficiently reconnoitered, the threat actor closed the VPN session. Less than 30 minutes elapsed between the initial access event and VPN session closing.
Three days later, DeepBlueMagic re-authenticated to the network using the same VPN credentials albeit with a new client hostname strongly suggestive of Windows from a new Tor node IP address. The threat actor picked up with they previously left off by remotely accessing the domain controller and from there attempting to remotely connect to C$ on select target servers over SMB. Later, PSEXEC was used to remotely execute an unknown file on at least one targeted server. The threat actor later executed the BestCrypt executable from a folder named “crypt” located in the C drive’s root directory. The victim later reported all client and server devices were all encrypted with Bitlocker.
Analyst Comments:
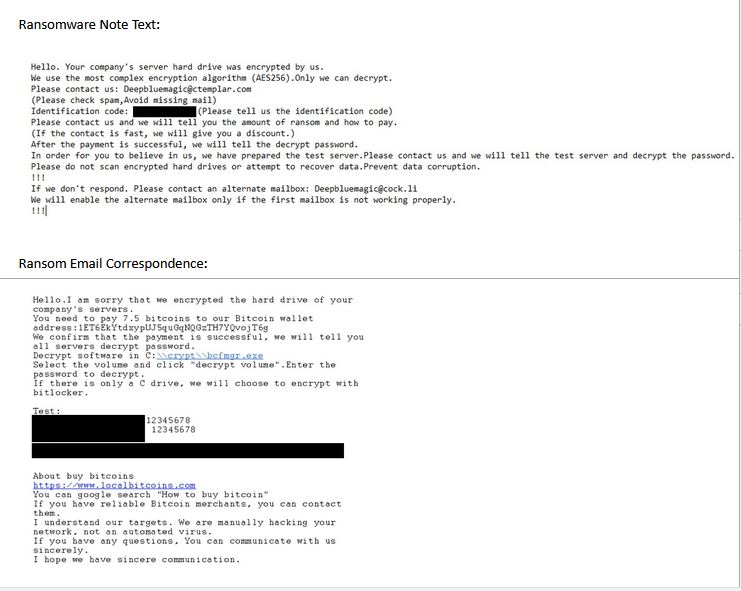
The DeepBlueMagic ransomware note text resembled samples of Romanain-speaking TimisoaraHackerTeam (THT). Everything from the note’s sentence structure to suggested means of purchasing Bitcoin, localbitcoins[.]com matched verbatim. The DeepBlueMagic threat actor recycled the message text and but swapped in their own account details suggesting a potential linkage between the gangs.
The threat actor’s exclusive use of living-off-the-land binaries (LOLbins) and freeware stood out to Antigen. The decision to use such tools, including Tor infrastructure, not only aided the threat actor in successfully compromising the victim network but also had the secondary effect of impeding attribution, and perhaps more importantly signature, at the operational level. LOLbins have been in vogue for over a decade by both low-sophistication threat actors and state-sponsored advanced persistent threats alike so little outside of the execution and file location of the BestCrypt binary for encryption purposes was particularly unique signature attributable to this ransomware family, as a result. Price Waterhouse Cooper (PWC) noted that barriers to entry are dropping as Ransomware-as-a-Service schemes proliferate. The DeepBlueMagic ransomware case observed by Antigen, although only a single datapoint, would seem to validate that theory with one caveat—time to achieve domain administrator user privileges.
Despite mostly unrestrictive egress policies prime for outbound C2 or massive data exfiltration observed in cases, DeepBlueMagic chose to instead parlay a user-level VPN connection into domain administrator rights from an ideal network vantage point in 17 minutes, a respectable time even for a professional penetration tester with ideal conditions. The threat actor may not have relied on a novel encryptor or custom C2 infrastructure but they were more than adroit enough with freely available penetration testing tools to be operational effective.
Adopting a “Do It Yourself” (DIY) Ransomware-as-a-Service (RaaS) revenue model would likely be attractive to interested RaaS affiliates. It eliminates the need for leasing software from a ransomware developer and settling for only a portion of the profit. A growing number high profile disputes and outright conflicts between prominent ransomware developer gangs and their own affiliates hint at growing tension within more precedented RaaS models. This DIY revenue model associated with DeepBlueMagic and similar gangs bear watching as it may represent an emerging RaaS trend.
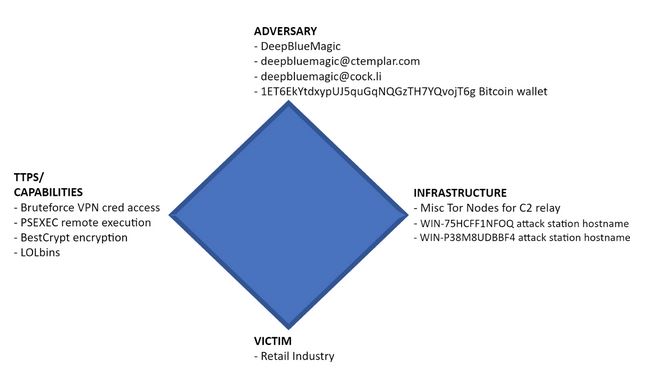
Atomic IOCs:
WIN-75HCFF1NFOQ attack station hostname
WIN-P38M8UDBBF4 attack station hostname
deepbluemagic@ctemplar.com
deepbluemagic@cock.li
ET6EkYtdxypUJ5quGqNQGzTH7YQvojT6g Bitcoin wallet