Case Summary
The Lockbit gang stands out among other ransomware-as-a-service peers for its sophistication relative to other RaaS gangs and affiliate operators. The ransomware itself could accurately be described as a semi-automated malware toolset capable of antiforensics, defensive evasion, network discovery, automated lateral movement and data exfiltration. Moreover, its affiliate operators have a reputation for conducting up tempo interactive operations and accomplishing objectives in a short amount of time relative to many peers.
Antigen Security was contracted to perform a compromise assessment with a manufacturing victim who experienced a Lockbit 2.0 ransomware attack in December 2021. Several workstations and all servers were impacted. Extensive disk evidence was available for all device infrastructure and firewall logs post-encryption.
The aim of this report is to contribute operational details discovered from Antigen’s own Lockbit 2.0 ransomware case including underreported techniques, tactics, and procedures that may help provide a more complete threat profile.
Lockbit 2.0’s Attack Chain
The Lockbit 2.0 affiliate operator’s means of initial access was a compromised username and password for a root-level user on Fortinet SSL VPN appliance protected by single factor authentication, as described by Fortinet. After the VPN appliance allocated a client IP, the affiliate operator pivoted directly to the Active Directory (AD) server over Remote Desktop Protocol (RDP). Later, the operators used RDP for another AD admin account to pivot to a different device.
PowerShell operational logs generated from the AD server indicated that the threat actor created text files strongly suggestive of AD discovery such as “email accounts <victim company name>.docx” and “list <victim company name> users and groups.txt.” The encryptor was deployed to several workstations and servers using a group policy object that installed a scheduled task on the destination device to periodically run the encryptor.

A known AD admin account was later used to pivot to another device via RDP. The executable file was named using a 6-character alpha numeric string taken from the unique “Decryption ID” in the ransomware note “Restore-My-Files.txt” that was generated as part of the encryption process.
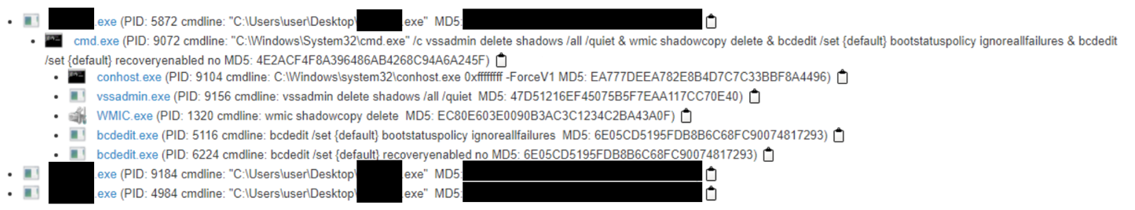
As we’ve seen in the past, the binary used bcdedit.exe to modify boot settings and gain persistence.
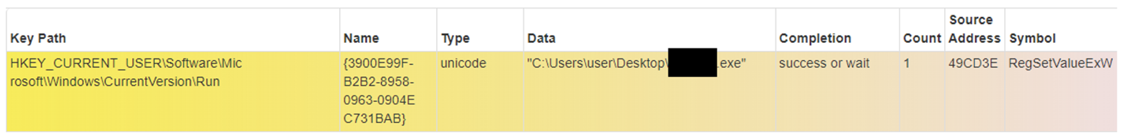
The infamous Lockbit_Ransomware.hta screensaver file was also present on some of the encrypted devices.
The Lockbit 2.0 affiliate operator then performed extensive file directory enumeration across several share drives, most of which were hosted among the server infrastructure. Later, the User Assist artifact logged a seemingly unique file called “Lockbit_<Decryption ID>.exe and seemingly self-deleted after execution. Antigen assessed this binary represents the Steelbit that is separate malware purpose-built for data exfiltration. The forensic timeline suggested that human driven on-net operations ceased within approximately 10 hours after network access was first established. Three days into the intrusion, and more than 36 hours from the initial encryption event, miscellaneous antivirus solutions installed across the network began flagging the ransomware.
The infamous Lockbit_Ransomware.hta screensaver file was also present on some of the encrypted devices.
The Lockbit 2.0 affiliate operator then performed extensive file directory enumeration across several share drives, most of which were hosted among the server infrastructure. Later, the User Assist artifact logged a seemingly unique file called “Lockbit_<Decryption ID>.exe and seemingly self-deleted after execution. Antigen assessed this binary represents the Steelbit that is separate malware purpose-built for data exfiltration. The forensic timeline suggested that human driven on-net operations ceased within approximately 10 hours after network access was first established. Three days into the intrusion, and more than 36 hours from the initial encryption event, miscellaneous antivirus solutions installed across the network began flagging the ransomware.
Analyst Comments
It is difficult to not be impressed by both the Lockbit malware’s functionality and its affiliate operator’s on-net speed. Not too long ago, these capabilities were more likely to characterize a state-sponsored advanced persistent threat rather than an increasingly prominent eCrime threat actor, but the times they are a-changing. Worm-able, or self-spread, ransomware is indeed upon us.
Yet, Lockbit 2.0’s relatively sophisticated tradecraft was evident throughout the case. Even after achieving domain admin, the operator affiliate took care to keep a small operational footprint by leveraging the GPO for follow-on propagation, rather than employ a respectable alternative living-off-the-land binary like terminal services for lateral movement. Instead of leaving the normal windfall of forensic artifacts behind like every other RaaS gang, the malware cleared event logs and self-deleted itself.
It is worth noting that neither of the aforementioned practices were necessary to ensure the attack’s successful outcome. Typical defensive tools are not going to flag RDP, so a data extortion situation was almost inevitable. Rather, the observed techniques were clearly employed as antiforensic measures, a higher order of operational sophistication and not characteristic of many RaaS gangs. Employing extensive defensive evasion measures, including plain old stealth, are no longer characteristic of only 1eet hackers and APTs—that rarefied space now includes RaaS. Defenders, take note.
The latent antivirus detections are particularly disappointing. Three reputable products all failed to detect executables with either the RaasS gang’s name and/or the word “ransomware” in the binary’s file name. It seems highly likely the gang is compiling new binaries for each victim based on regular use of unique decryption ID string components in most of their executable’s name so understandably, pattern matching of a known malicious hash is not a viable means of detection. Still, it stands to reason that even traditional antivirus products should be include detection logic looking for highly suggestively named Windows portable executables that exhibit destructive behaviors such as “cmdline: vssadmin delete shadows /all /quiet.”
Get Help from Our Experts
As sophisticated attacks such as Lockbit 2.0 become more common, it’s important to be prepared with an incident response plan. Antigen Security can help you determine the next steps in the aftermath of an attack. Schedule a meeting with one of our experts to get started.
(NOTE: To preserve the identity of the victim, Antigen is deliberately not including either a diamond model or atomic IOCs with this report)
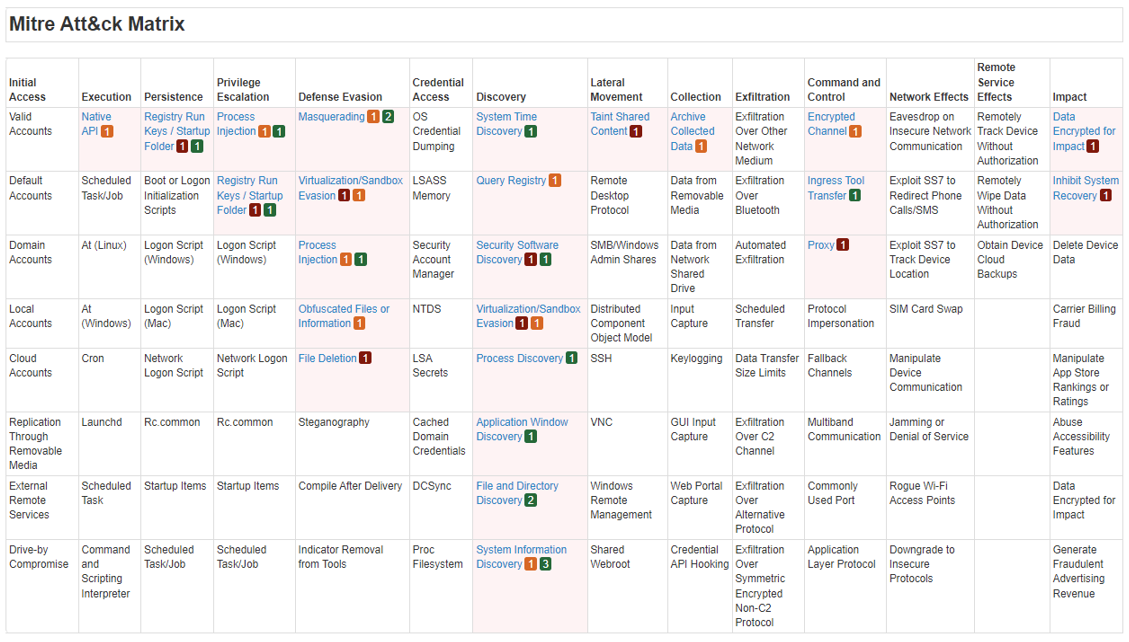
Figure 1: Lockbit 2.0 Encryptor representation on Mitre ATT&CK Matrix based on dynamic analysis
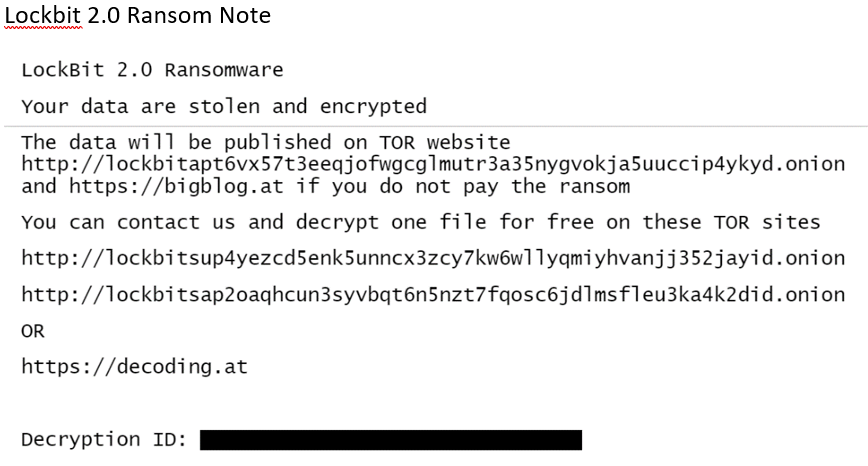
Figure 2: Lockbit 2.0 ransom note
