Conti consistently ranks among the more successful Ransomware-as-a-Service gangs in the game. Also known as FIN12 and Wizard Spider, the Saint Petersburg, Russia-based gang has gained notoriety for extorting millions from their victims most notably those in the Healthcare sector.
Antigen Security was contracted to perform a compromise assessment and recovery of a ransomware victim company belonging to the North American manufacturing sector. Even post-encryption, extensive disk evidence was available for all server infrastructure and firewall logs.
The aim of this report is to contribute operational details discovered from Antigen’s own Conti ransomware case including underreported techniques, tactics, and procedures that may help provide a more complete threat profile.
Summary of Observed Events
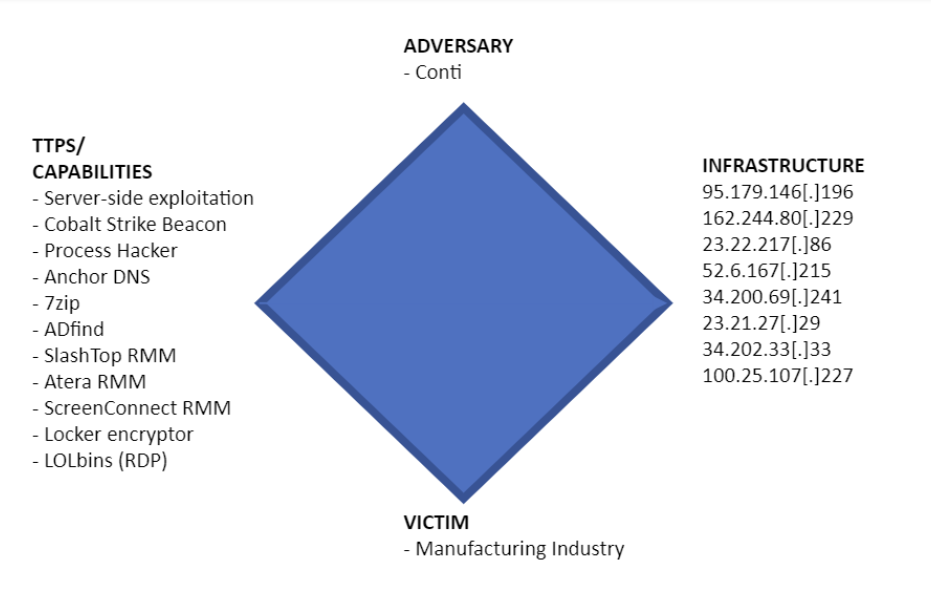
Antigen assessed that the Conti threat actor achieved initial access to the victim network by exploiting one of the DEVCORE ProxyLogon family of Exchange vulnerabilities shortly after Microsoft released the corresponding KB5000871 patch. The vulnerable web server was then implanted with a backdoor webshell (shell.aspx) to help main network access. Fifteen days following the initial implantation event, the threat actor returned to the Exchange server via the webshell and installed Anchor DNS and ScreenConnect, two tools popular with Conti intrusions and other RaaS gangs.
With redundant means of persistence now achieved the threat actor disconnected and four months elapsed. When they did additional intrusions tools such as 7zip.exe, ADfind.exe, and additional remote monitoring and management applications, Atera and SplashTop, were installed.
A ScreenConnect session was established as the initial means of command and control (C2) directed at IP address 95.179.146.196 and from said session Cobalt Strike Beacon C2 was executed with the outbound connection directed at attacker infrastructure located at malicious URL http://fivezin[.]com/jquery-3.3.1.min.js over both TCP:80 and TCP:443 in a similar fashion to the method described by TheDFIRReport.com. The threat actor relied on Remote Desktop Protocol (RDP) to move laterally to assorted server devices and perform system-level discovery including a host named after a well-known disk backup and recovery software as well as a hostname strongly suggestive of being part of the victim’s backup capability. Data exfiltration was made possible using a Scheduled Task configured to execute Anchor_x64.exe from the victim’s mail server.
After nine days of sporadic human-operated intrusion activity, the threat actor dropped and executed a script named “start.bat” from a Windows server containing automation logic that established remote administrative shares with each Window devices on the domain, placed the encryptor Locker.exe, and executed it. Thousands of files on each affected Windows device were subsequently encrypted, however the operating system remained operational unlike with DeepBlueMagic. Behavior strongly suspected of representing data exfiltration from the Exchange server commenced the day after the encryption event via Anchor_x64.exe with outbounds connections directed to various IP addresses registered to Amazonaws.com over TCP:80.
Analyst Comments
Registry entries found on the victim company’s Exchange server and initial access point indicated that the device was patched prior to the webshell implantation event. More interestingly, the Exchange server contained no evidence of ProxyLogon-specific remote code execution (RCE) IOCs within the IIS logs suggesting something other than the original ProxyLogon RCE may have been used to achieve initial systems access. (Note, media would later link Conti to a derivative vulnerability called ProxyShell in August 2021.) At least one other source reported that Conti leveraged another actor’s webshell on patched systems. Both the timing and pattern of behavior of Antigen’s case align with this observation.
One might glean from the chronology of events that Conti leveraged a contemporary 0-day server-side exploit to gain initial access in effect prepositioning network access to a momentarily vulnerable public-facing device until the RaaS gang had resources to compromise the entire network. But that theory ignores the increasingly complex system of crimeware whereby multiple actors typically organized along functional specializations or collective affilation transact with one another in the normal course of financially-motivated criminal intrusions. Conti ransomware intrusions were reported to transpire over weeks rather than months, according to Mandiant and SOCRadar. It seems more likely an independent access broker performed the initial exploitation and implantation and resold the access to a Conti affiliate. If true, this would represent a deviation from better known Conti attack chains.
Diamond Model
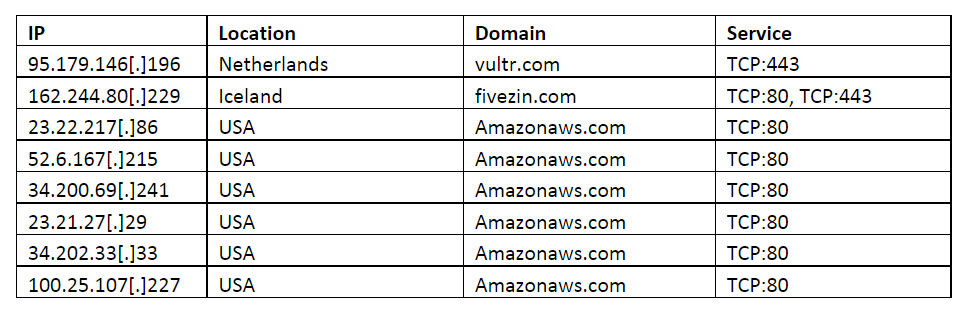
Atomic IOCs:
Conti Ransomware Note